October 2023 Patch Tuesday
There's been a long string of zero-day events through September and into the October Patch Tuesday lineup. Apple had five zero-day vulnerabilities across most of their products culminating in their updates that were released on September 26th (which also included the EoL of Big Sur).
Google and Mozilla continued to be busy with several zero-day vulnerabilities in the open-source library, Libwebp. This also impacted chromium-based browsers like Microsoft Edge, Opera and others. For more details on the lineup of CVEs leading up to October Patch Tuesday, check out our Patch Tuesday Forecast on HelpNetSecurity.
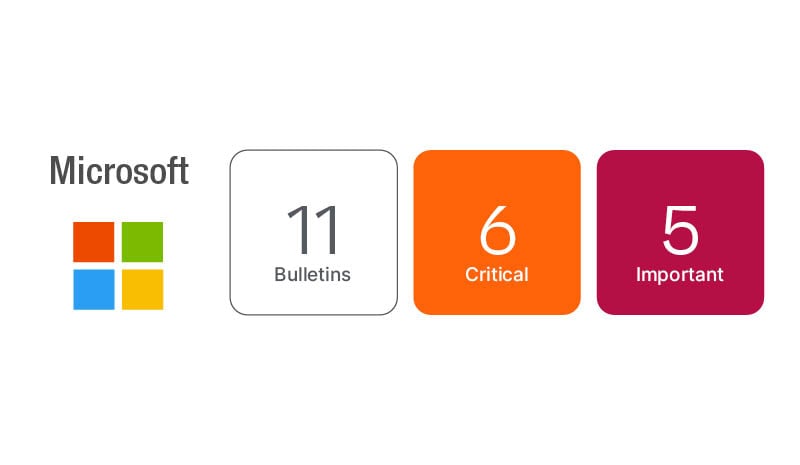
Microsoft has resolved 104 new CVEs this month, three of which are flagged as exploited. The lineup from Microsoft includes Windows, Office 365, SQL Server, Exchange Server and multiple Azure components. Along with the large lineup of fixes, October also marks the end-of-life for Windows Server 2012 and 2012 R2.
Microsoft zero-day vulnerabilities
- Microsoft has resolved an Elevation of Privilege vulnerability in Skype (CVE-2023-41763) which allows an attacker to send a specially crafted network call to a target Skype for Business server. The network call could cause the parsing of an http request made to an arbitrary address. This could disclose IP addresses or port numbers or both to the attacker. The CVE is rated as important and has a CVSSv3.1 of 5.3, but proof-of-concept code has been disclosed and there are exploits detected in the wild. This CVE should be treated as a higher severity than Important due to the risk of exploit.
- Microsoft has resolved an information disclosure vulnerability in WordPad (CVE-2023-36563) which allows the disclosure of NTLM hashes. The CVE is rated as Important and has a CVSSv3.1 of 6.5, but proof-of-concept code has been disclosed and there are exploits detected in the wild. This CVE should be treated as a higher severity than Important due to the risk of exploit.
- Microsoft has resolved a Denial of Service vulnerability in the HTTP/2 protocol (CVE-2023-44487) which allows request cancellation that can reset many streams quickly. The vulnerability has been exploited in the wild since August. The vulnerability has been resolved in the Windows OS and in Visual Studio, .Net and ASP.Net. The CVE doesn't have a CVSS calculated, and Microsoft’s severity is only rated as Important, but due to active exploitation this CVE should be treated as a higher severity.
Windows Server 2012\2012 R2 and Windows 11 21H2 end-of-life
This patch Tuesday will include the latest updates for Windows 11 21H2 and Microsoft Server 2012/2012 R2. The later go into Extended Security Support (ESU) starting with a November release, and Microsoft also announced the keys used to enable these updates will be managed as part of Azure Arc. They should be released next week.
End-of-life software poses a risk to an organization. No public updates will be available for these OS versions going forward. For Windows 11 users, this means upgrading to a new Windows 11 branch. For Server 2012\2012 R2 it'shighly recommended to subscribe to ESU or migrate to a newer server edition.
Linux zero-day vulnerabilities
- CVE-2023-42115 has a whopping 9.8 CVSS and affects the Exim software solution, a message transfer agent (fancy way of saying email server) that’s very popular on Linux (including web hosters), which wasvulnerable to remote code execution. This vulnerability had been reported for over a year to the original developers but never addressed properly and is now public. There's exploit code available in the wild. It particularly affects servers configured with centralized identity management, including in mixed Windows/Linux environments with Active Directory.
- Exim announced on October 2nd that a security update for exim-4.96.1 and 4.97 has been created to mitigate this CVE and two other zero-days (with three other zero-days remaining unpatched). Exim is an important MTA software because it’s bundled with “control panel” web hosters, including in docker images.
- CVE-2023-4863 is a 9.1 CVSS heap-based buffer overflow that affects libwebp, which is a library used by countless applications (for example Google Chrome, Firefox or Brave) to render images on screen. It's beenfound to be vulnerable to an exploit, which is already in the wild, and all the applications using it'll be affected — which are essentially any applications that show or process images in the "webp" format (or its derivatives). This is remotely exploitable and requires no interaction to trigger – simply viewing a malicious image is enough to trigger it.
Linux vulnerabilities can have a long tail, from the publishing of the CVE to patches being made available by Linux distributions. To monitor the latest Linux CVEs, check out TuxCare’s detailed CVE Tracker.

