Evolving Your Security Strategy Toward Self-Securing With Ivanti Neurons
 Threat actors move fast. They are agile and will shift tactics as opportunities present themselves. As the COVID-19 pandemic changed how we had to work and manage our users and environments, threat actors also made changes. They adapted to a new opportunity and they did so very quickly. ZScaler released a report in April showing the increase in COVID themed attacks increasing 30,000% between January and March this year. In just a few months, threat actors made a wholesale shift in tactics to take advantage of a large opportunity. Now that is business agility that many of us can only envy.
Threat actors move fast. They are agile and will shift tactics as opportunities present themselves. As the COVID-19 pandemic changed how we had to work and manage our users and environments, threat actors also made changes. They adapted to a new opportunity and they did so very quickly. ZScaler released a report in April showing the increase in COVID themed attacks increasing 30,000% between January and March this year. In just a few months, threat actors made a wholesale shift in tactics to take advantage of a large opportunity. Now that is business agility that many of us can only envy.
According to a research study from RAND, threat actor can exploit a vulnerability in a median 22 days and most exploits will have a shelf life of 7 years. An annual report from Recorded Futures that shows the most commonly exploited vulnerabilities from 2019 confirms this. Most exploits are compromising vulnerabilities that have been around for some time.
How do we counter this level of agility and adaptability from threat actors? By adapting ourselves. We need to shift toward a self-securing strategy. Yes, threat actors are gaining in sophistication, but at the root of that sophistication is the same tactical execution that they have been doing for years. Reconnaissance, exploit vulnerabilities, gain persistence, move laterally, exfiltrate/encrypt data. They are performing the same activities, just with more automated and augmented capabilities.
What do we mean by self-securing? Through analyzing attackers' methods and the use of automation and machine learning we can react more quickly to real threats. This adaptive security approach is made up of three parts: Sensing, Prioritization, and Remediation.
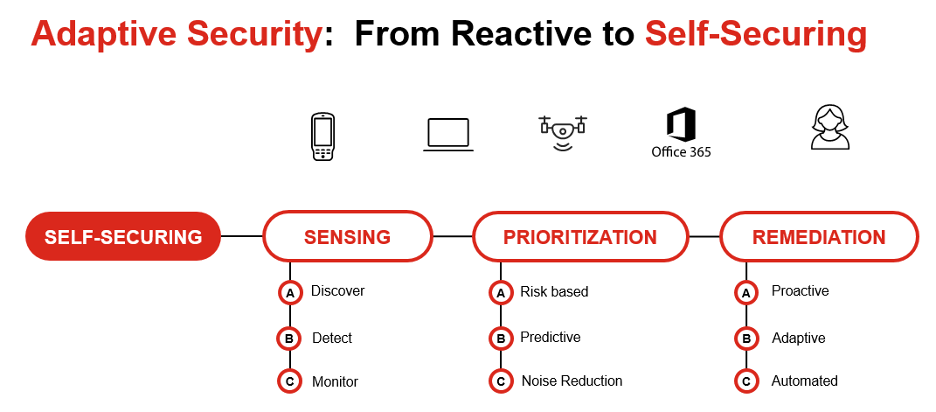
Sensing
Discover what is in your environment. Detect running software and configuration and analyze for vulnerabilities. Continuously monitor for changes; new devices being introduced and changes in state of devices in the environment.
Prioritization
Risk-based prioritization to identify what is actively being exploited and respond to highest risks quickly. Predictive algorithms to anticipate changes and threats and give prescriptive guidance on what to do next.
- Noise reduction: There is always way to much data and way to many threats to manage everything, but that noise can be reduced to the critical activities that will mitigate the most risk quickly.
Remediation
Acting is the most critical part of the process. Identifying thousands or tens of thousands of threats does no good if action is not taken to eliminate those threats.
- Proactive: As we discussed earlier, threat actors move quickly. We need to be proactive in our responses. The prioritized risks can quickly bubble up to be responded to first. Knowing what is being actively exploited helps optimize remediation efforts.
- Adaptive: Our remediation capabilities (as well as assessment) need to be able to adapt to the environments and circumstances. The COVID pandemic is a good example of why this is necessary. As we rapidly shifted to a remote workforce, it is essential that our security capabilities can follow. Public or private clouds, on premises or off premises user systems, corporate devices or BYOD, we need to ensure we can manage and respond to threats to our environment. Finally, we come to Automation.
- Automation: Threat actors are automating more and more of the attack. This means it can happen fast and at scale. We need to automate the response. Automating the steps, reducing time between steps, and removing human elements wherever possible increases response times and eliminates errors.
The biggest thing to keep in mind is that self-securing does not mean the human is eliminated from the equation. It is a focus on automating activities that can be automated, generating the analytical data needed to make decisions quickly and prioritizing actions for analysts to quickly approve and respond to urgent threats in a timely fashion, which again would be automated.
Learn more about Ivanti Neurons here.

